Post-COVID 19: What to Implement When Work from Home is Here to Stay?
Ever since the pandemic outbreak, working from home has become a daily routine for most of us already. Some say working from home dramatically improved their productivity and others say it made everything harder. From cooperating to communicating with team members and partners have become merely possible due to physical limitations and access controls.
However, many companies have actually announced plans to maintain the new norm, or even optimize work schedules. It’s no surprise that remote working and virtual meetings will be the main method of communication even when the coronavirus crisis passes in the near future.
Building a Safe Working Environment
Employees demand an IT environment where they can send and receive data safely at anywhere and anytime. Due to the increased cyber-attacks across industries, there are growing concerns about cybersecurity and the solutions that could be helpful to different business environments.
According to a global security firm Check Point, 95% of respondents said that the actual number of threats and attacks have increased since the corona outbreak. They also pointed out that there still are limitations when it comes to providing a secure remote access solution and resolving restrictions on the use of unauthorized software.
This new working environment has brought different challenges to businesses and without proper measurements, devices including personal computers, and devices outside the scope of management that are capable of accessing work servers can be a serious threat to a company’s cybersecurity.
The New Normal, Telecommuting Solution for Post-COVID19 Era
Despite small and big security threats, deployment of cybersecurity solutions is what is making this new transition actually feasible. It’s quite common for large corporates and public institutions to provide separate networks for external and internal use. If you need to access the work server from home, you might have to use a VPN (Virtual Private Network) in this case. VPN is a communications technology that allows users to remotely access a server by creating an encryption tunnel through data encryption.
However, VPN does not support malicious traffic blockings and it has a high possibility of being exposed to abnormal attacks. Additionally, VPN’s ID and PW based authentication method can be quite vulnerable. In order to utilize VPN on different devices, it is also required to install a separate program – let’s take a look at some of the solutions that don’t require installing a VPN or different programs on your devices.
Remote Access Software Solutions During the Pandemic at a Glance
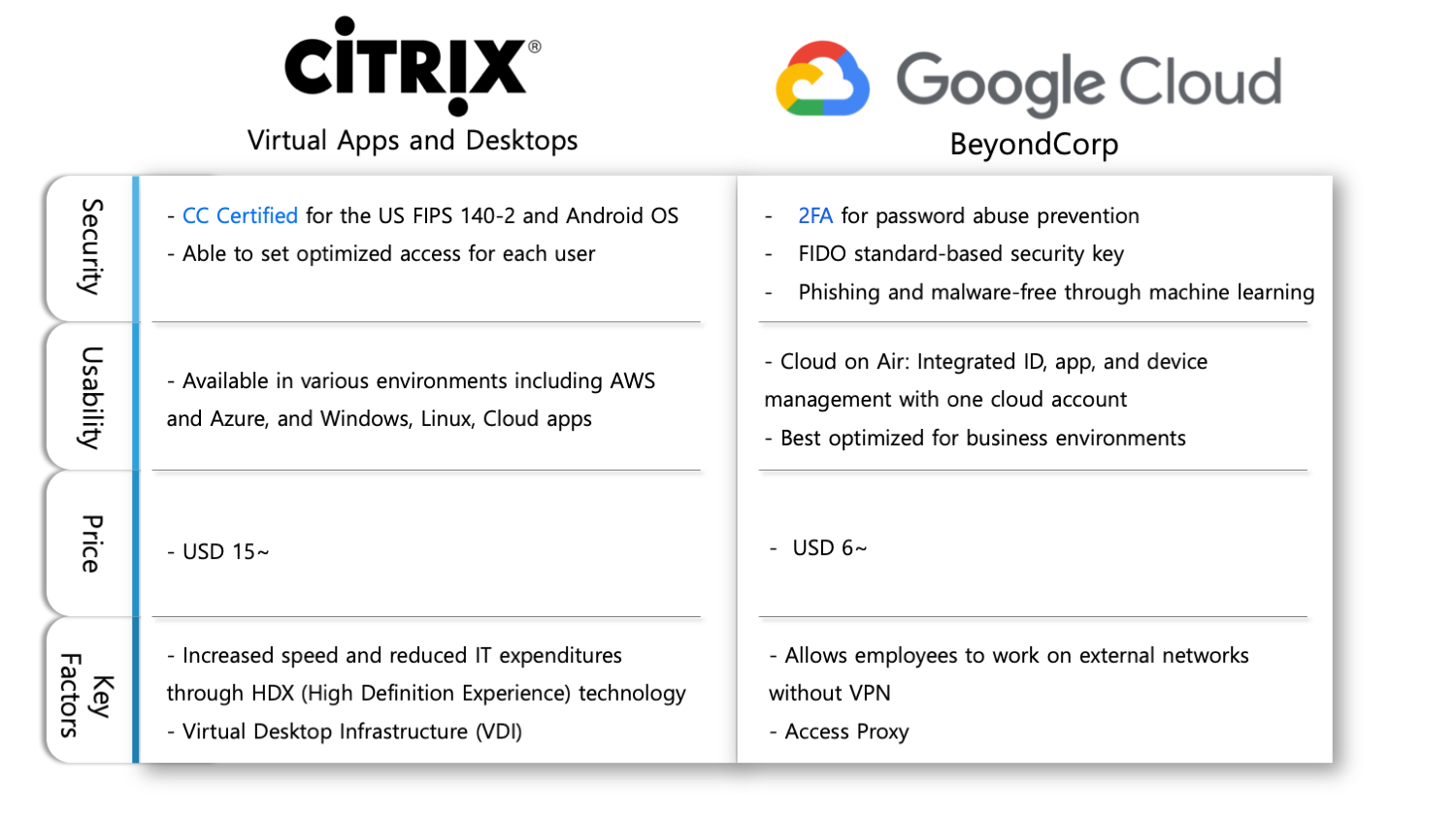
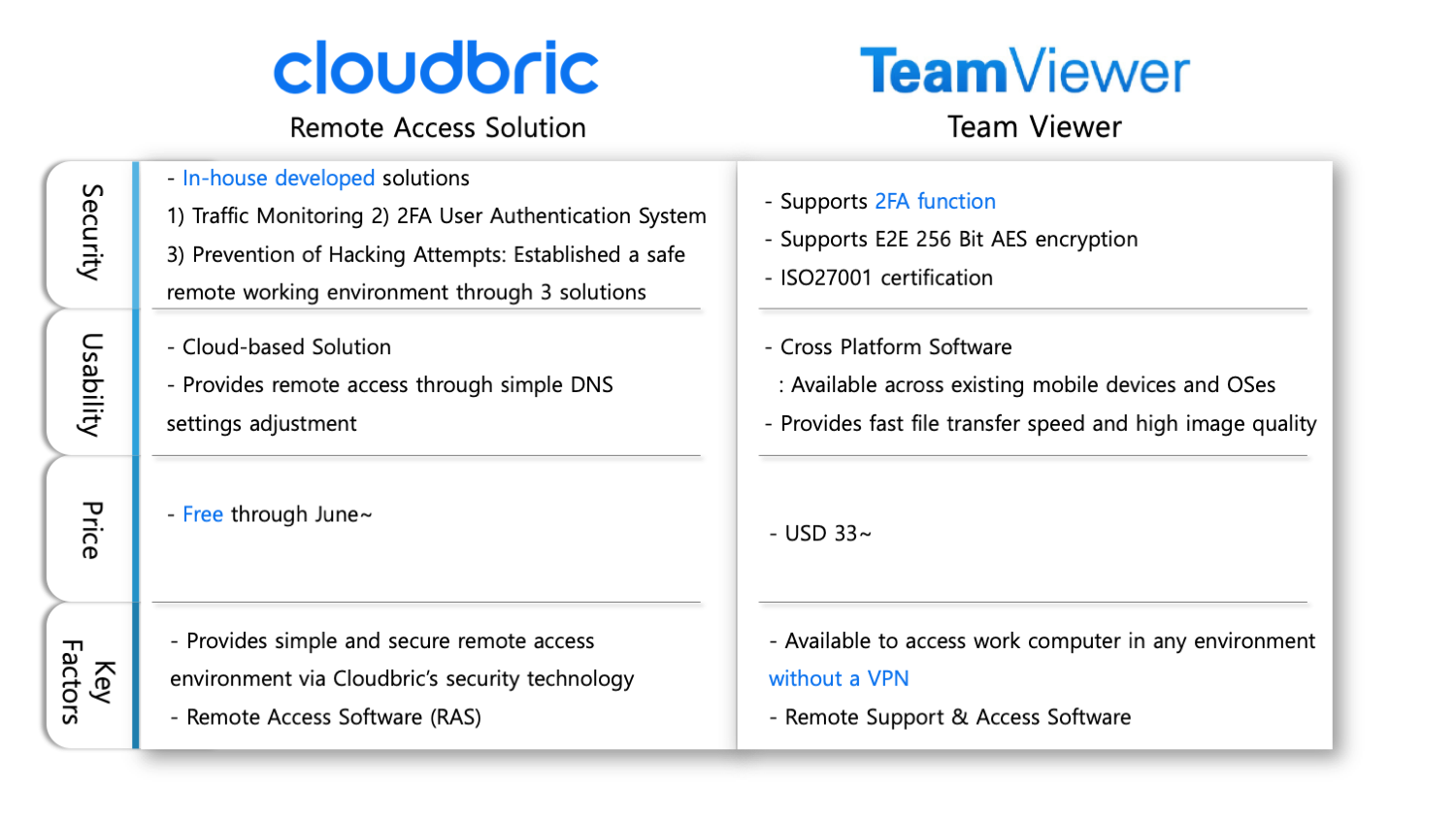
We should bear in mind there’s no such thing as the safest or the most efficient remote access software solution when it comes to protecting your business. Most importantly, costs should also be taken into account in order to establish a stable remote access environment. If you wish to try out Cloudbric’s free software trial, feel free to contact Cloudbric for more information and deployment.
