What Is a Reverse Proxy and What Does It Mean to Enterprise Security?
What Is a Proxy Server?
At the most fundamental level of internet communication, whenever a client (user) makes a request to a web service (website or web application), the client’s computer sends its request over the Internet directly to the web server. The web server then processes the request and sends the requested resources to the frontend of the user interface.

However, in reality, the communication procedure is rarely this simple. More often than not, a proxy server is added to the process. A proxy server is an intermediary located in between the client’s computer and the web server. Whenever the client makes a request, the proxy server serves as a middleman that intercepts the request and then communicates the request to the web server on behalf of the client.
A proxy server can be a useful tool for both the client and the server. When the client deploys a proxy server in front of its computers, it is called a forward proxy. On the opposite end, when the web service provider deploys a proxy server in front of its web servers, it is called a reverse proxy. Simply put, a forward proxy is implemented and controlled by the client, while a reverse proxy is implemented and controlled by the web service provider.
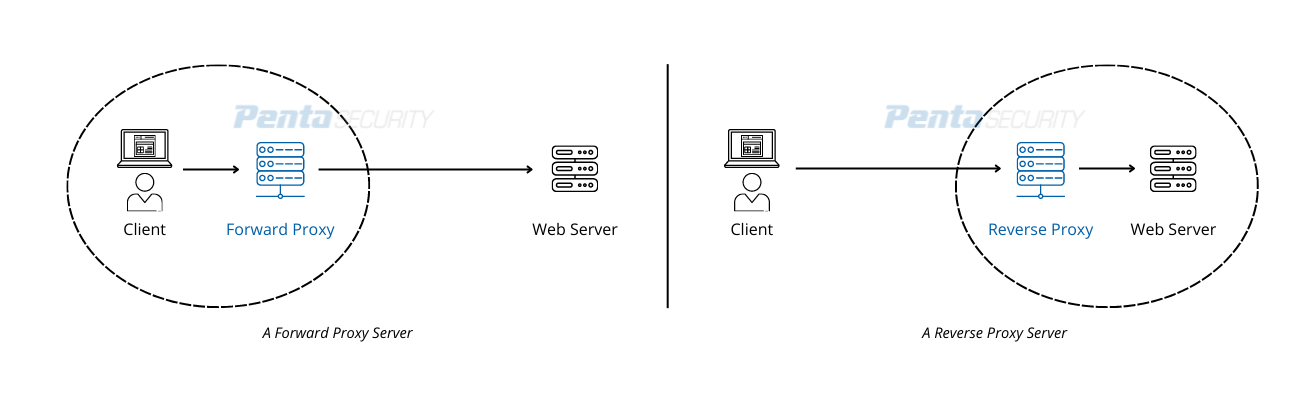
Reasons to Deploy a Forward Proxy
But why would a client want to deploy a forward proxy? First, a forward proxy server can be used by the client to bypass certain restrictions set out by either their own network administrator or the provider of the web service it wants to access. For instance, some governments and organizations use firewalls to block their clients’ computers from accessing certain content outside their country or organization. By deploying a forward proxy in a configuration that isn’t restricted by the administrator, the client would be able to send the request via the proxy server to the web service. Network administrators usually use forward proxy servers to grant certain people access to restricted websites that others are not allowed to access.
Similarly, an individual or enterprise client can also purchase and deploy their own forward proxy servers to bypass their government’s restriction, as commonly seen in countries with strict internet censorship. In this case, the forward proxy tends to be a remote proxy located outside the country, serving the same purpose as the more familiar VPN (virtual private network), except that a forward proxy only intercepts requests for certain selected web services, while a VPN intercepts all internet communications. In this scenario, the forward proxy also protects the client’s privacy. If an individual or organization wants to hide its IP address from a web service provider, it can set up a forward proxy server in a remote IP address, then forward all requests to the web service via the remote proxy. This setting prevents others from tracking down the client’s identity.
Conversely, a forward proxy server can also be deployed by a network administrator to prevent individual clients from accessing certain web services outside its network. This is done by applying filtering rules to the proxy server, so that the forward proxy would refuse forwarding requests to banned websites and services. Schools and enterprises usually use this method to block their students and employees from sending requests to (i.e., accessing) social media or online shopping sites. This same technique can be used by governments as well to prevent citizens from accessing illegal content.
Reasons to Deploy a Reverse Proxy
Unlike a forward proxy, a reverse proxy is deployed by the administrator of the web service, oftentimes used by organizations to manage and protect their web servers. In this case, the administrator installs the reverse proxy in front of its web servers. All requests coming from the clients will be intercepted by the reverse proxy before being forwarded to the web servers.
Although forward proxies and reverse proxies have the same technical mechanisms, they serve very different purposes. The primary reason a web service provider would want to deploy a reverse proxy is for security. Since all client requests are intercepted by the reverse proxy, the IP address of the web servers is always kept hidden from external parties. This protects the web servers from directly facing DDoS (distributed denial-of-service) attacks. Attackers would only be able to target the reverse proxy, which is usually equipped with better security measures to block and filter botnets.
Popular websites and web services must be built on top of multiple servers as one server is not enough to handle the tremendous requests. In this case, a reverse proxy server can be configured to evenly distribute requests to these web servers in a process called load balancing, preventing the situation where all traffic is fed into one server. Also, in case one of the web servers fails, the load balancer would be able to direct traffic to the remaining servers to ensure that all requests are properly handled and services are not disrupted.
A web application firewall (WAF) is a common type of reverse proxy, specifically designed to filter traffic and protect web servers from attacks. Deployed by the web service provider, the WAF sits in front of the web servers and intercepts all incoming client requests, then analyzes the requests to filter out any malicious attempts. Conventional WAFs use signature lists to filter requests. However, matching every request with a long list of signatures has been known to slow down the response speed and hinder the user experience. This is why the latest generation of WAFs like Penta Security’s WAPPLES use a set of logical rules built on algorithms derived from machine learning to effectively filter out malicious traffic, without slowing down the web service. This detection mechanism is also known for having extremely low false-positive rates.
WAPPLES can be installed in a network with an existing remote proxy (remote proxy mode) or installed as a standalone remote proxy itself (inline mode). Not only does it protect the web servers from all types of OWASP Top 10 vulnerabilities and zero-day attacks, but it also acts as a load balancer to help distribute traffic and ensure application stability.
For more information on security implementation, check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Database Encryption: D’Amo
Identity and Access Management: iSIGN+
Automotive, Energy, Industrial, and Urban Solutions: Penta IoT Security
For detailed inquiries, contact Penta Security’s security consulting team.
