How to Protect My Accounts from Hackers with MFA Solution
Have you ever thought about the maximum number of accounts you can create online? There are probably at least five to ten different accounts across various websites for each person nowadays. As the advantages of the Internet expand and the use of websites increases, it has become a thing for people to use different IDs and PWs to access various websites for different purposes. However, the ID and PW we use are considered way too simple for what it actually does, and the reality is that it is insufficient to feel that using different passwords is the most secure way to protect our accounts from hackers.
Then what can you do to keep the accounts you have safe? Do you need to set different IDs and PWs for each account? Should we create more difficult and complex passwords and change them often enough to bother hackers? But most definitely, it is known that the most effective and safest way to protect your account is to deploy a multi-factor authentication method for your organizations and furthermore, for your users. Let us take a closer look at how an MFA solution works and how it can protect us from hackers.
Why Deploy an MFA Solution?
The password most people are using right now is just not enough to fully protect the many accounts that contain personal information. In fact, many Internet service providers recommend creating complex passwords that include uppercase and lowercase letters, special characters, and passwords without continuity and periodically changing passwords when generating them.
However, according to a survey conducted by the FIDO Alliance in 2020, 60% of respondents who took part in the survey had 30 or more accounts, and about 70% were using two to five different passwords. 42% have experienced online account hijacking and of course, password security enhancements aren’t as ineffective, but as mentioned earlier, it is virtually impossible to create and use complex passwords for each account. As hackers continue to attack users’ passwords and accounts, it has become a necessity for organizations to deploy other security measures in advance.
Security Enhancements
Multi-Factor Authentication (MFA) security literally refers to the multiple verification methods applied to accounts after the user has authenticated themselves via existing ID and PW. In other words, it acts as double security by authenticating the user with an additional method other than PW.
By using several additional authentication methods in addition to the existing basic account information input, users can not only protect their identities but also increase the security of their organizations. Looking at the different authentication methods, if there were ID/PW method and PIN method that compare the knowledge between authenticators and verifiers as basic authentication methods, MFA mainly includes a separate medium containing the unique information, for example, security. Biometric authentication using tokens, mobile phones, security cards, OTPs, or biometric information such as a user’s fingerprint, iris, face, and voice is being used more and more frequently.
MFA Methods in Our Daily Lives
MFA security is important because it basically strengthens the security of individuals in their daily lives. In fact, it is easy to find websites that already applied two-factor authentication security for the same purpose. As Google is the representative search engine used by many people across the globe, they have managed to deploy a well-equipped MFA security system for users.
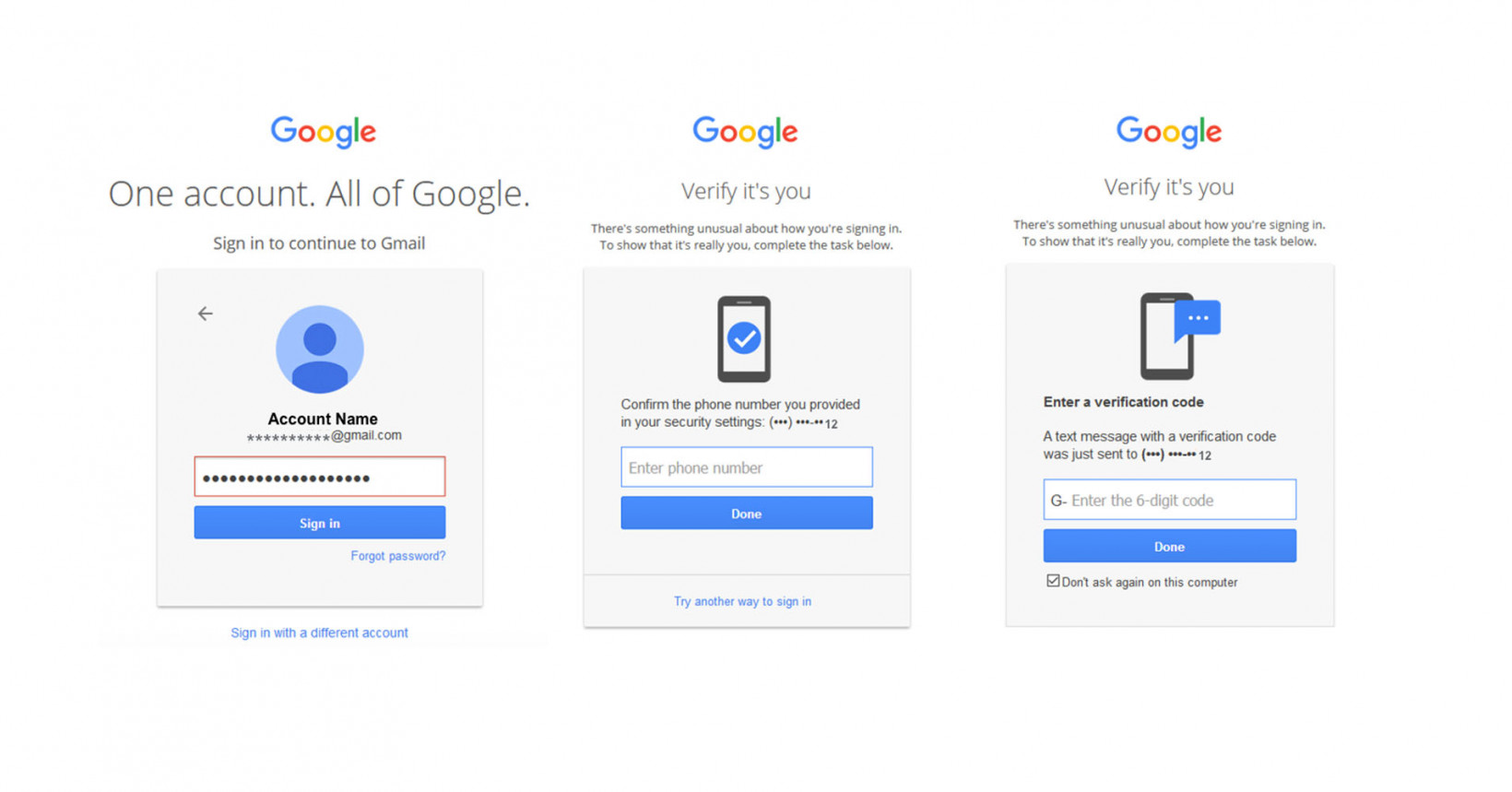
Google usually goes through a two-step verification (TSV) process through their app or users’ smartphones. As shown in the figure, the above screen pops up to allow users to verify themselves via authentication. In particular, it can be seen that secondary authentication security is practically helpful in a way that it is possible to report and track suspicious logins without allowing them to log in. In addition, you can set up two-step verification methods on messengers or social media accounts such as Twitter and Instagram as well.
MFA Solution for Enterprises
Recently, ransomware attacks using random substitution of personal account information, rather than the case of hacking the internal system itself, are becoming a major problem across the world. It can be said that the impact of the rapidly changing work environment along with the pandemic has had a major impact on this trend.
As working from home increases, personal security has become the security of the organization. Therefore, even within the organization, it is critical to deploy a security system that is suitable for the new user environment. To overcome the limitations of ID/PW for personal information protection, there are a few things an organization should check before deploying an MFA solution.
1) Interoperability between essential elements such as policy server, authentication server, and management tool for easier maintenance
2) Supports various authentication methods considering user environment such as multiple operating systems
3) Reliable and strong security such as FIDO authentication
4) Costs due to complex systems and updates, such as introduction cost and maintenance cost
During the stage of strengthening and building the entire security system, it is important to check whether the solution fits the purpose of the organization.
Penta Security’s Integrated Authentication Platform iSIGN+
Penta Security provides products that satisfy all the elements of an MFA solution, such as functionality, reliability, efficiency, maintainability, and interoperability, based on security technology accumulated over decades. The authentication platform iSIGN+ provides multiple authentication functions using mobile OTP, APP, PKI, and FIDO to secure authentication reliability and through in-house resource access control and user background check.
The paradigm for safer security is constantly changing, with Google making moves to set two-step verification as the default. Keep in mind that to protect the users as well as the entire organization through reliable security solutions, it is critical to deploy a secure MFA solution and other security measures such as the web application firewall to improve the overall security performance. Learn more about iSIGN+ here today.
