IaaS, PaaS, SaaS: Understanding Their Differences and Choosing the Right Cloud Security Solutions for Your Business
The enhanced speed, reliability, and availability of today’s internet connections have facilitated the rapid growth of the cloud computing industry. It has become incredibly fast and easy to perform and share complex tasks online anytime at any place. For most businesses, the amount of work done in the cloud has been increasing at an astonishing rate.
Cloud computing services have tremendous benefits. With centralized management and shared infrastructure, they save tons of time and resources in aggregate. More importantly, cloud computing made it possible for remote workers to collaborate anywhere across the globe, a need that is continuously growing, especially with mandatory social distancing during this coronavirus pandemic.
Recent research has shown that about 94% of organizations use some kind of cloud computing service, and that 83% of all organizations’ workloads are performed in the cloud (Hosting Tribunal). What’s more, over 60% of those looking to purchase software programs only demand cloud-based products, while less than 2% specified that they only want on-premises products (Software Advice).
Types of cloud computing services
Cloud computing services are offered in a variety of forms that are quite different from each other. Likewise, each form requires a different level of security measure. This may seem confusing at first, but as long as we understand the breakdown of the components of a cloud system, managing them can be fairly easy.
Based on the components offered, cloud computing services can be classified into three general categories. These are:
- IaaS (infrastructure-as-a-service),
- PaaS (platform-as-a-service),
- and SaaS (software-as-a-service).
Before digging deeper into each type of cloud service, let’s take a look at all the components of a cloud-based IT system. As shown in figure 1, a cloud system can be divided into nine layers, starting at the bottom with the network, storage, and servers, all the way up to the database and application layers.
For an on-premises IT system (first column on the left), the user takes full responsibility for all layers of the system, from setting up the network to installing the operating system, and to managing the database and application.
For the three types of cloud-based systems (the next three columns), the user shares a varying degree of responsibility with the cloud provider, depending on the service type.
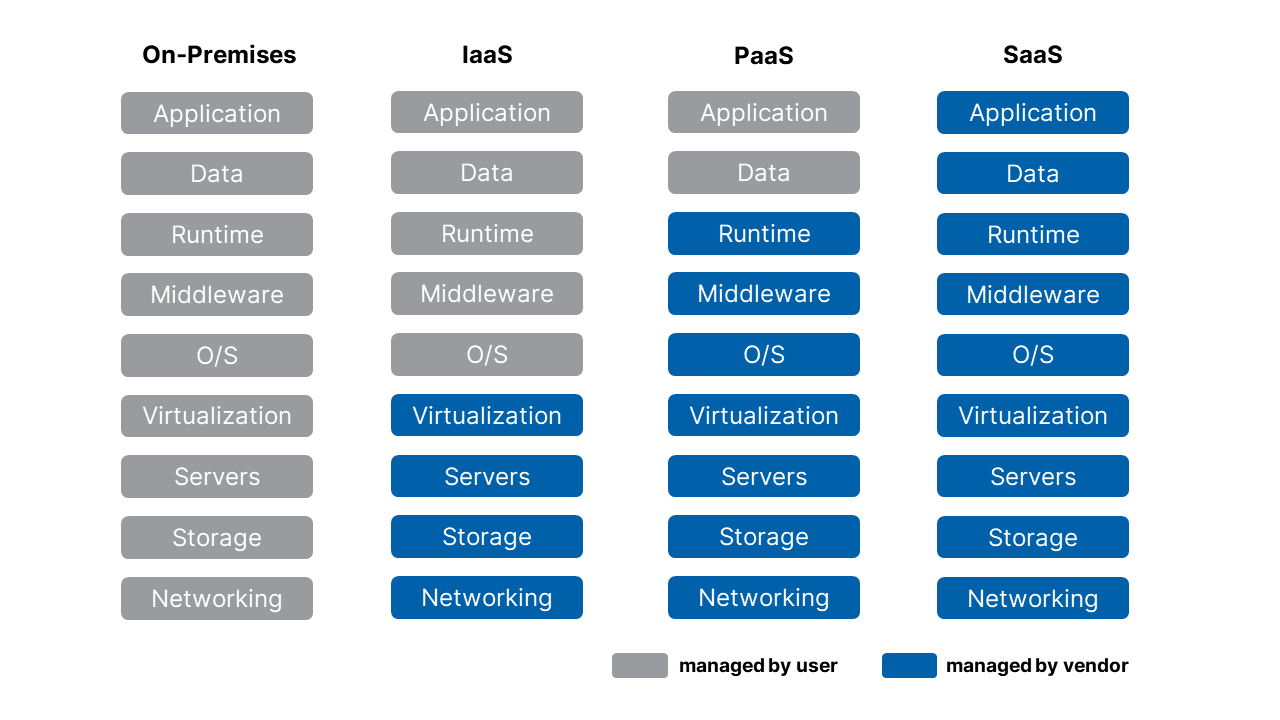
Figure 1: Split of Responsibilities for Each Type of Cloud Computing Service
IaaS (Infrastructure-as-a-Service)
IaaS is the most basic level of cloud computing service. In this case, the user borrows the provider’s infrastructure, usually networking hardware, storage, and servers, through the Internet.
Examples of IaaS providers include Amazon Web Services (AWS), Microsoft Azure, Google Compute Engine, and DigitalOcean.
The main advantage of IaaS is that the user has a lot of freedom on how they want to utilize the infrastructure. For instance, they can create virtual machines (VMs), install operating systems in the VMs, build databases, and create storage buckets.
PaaS (Platform-as-a-Service)
For PaaS, the cloud provider offers all the components that an IaaS offers, plus the operating system, middleware, and in many cases development tools, business intelligence services, database management systems, and other features.
Examples of PaaS providers include AWS Elastic Beanstalk, Windows Azure, Google App Engine, and Heroku.
Under a PaaS environment, the cloud provider offers the hardware, operating systems, and middleware, while the user is responsible for designing and operating their own web application and services. However, the vendor usually offers full support for the complete web application lifecycle, including building, testing, managing, and updating.
SaaS (Software-as-a-Service)
SaaS offers the complete package of a web application program. A SaaS provider manages all system layers from hardware to applications, so that all a user needs to do is to sign on and use the application. Most SaaS programs allow direct access from a web browser.
Most people are familiar with SaaS programs. Some examples of them include Microsoft Office 365, Google Apps (e.g. Gmail, Drive, Docs), Dropbox, Salesforce, and Adobe Creative Cloud. A SaaS program is usually purchased in the form of a subscription. These services are especially useful for remote work and education. Research has shown that the global SaaS market is expected to grow 13.1% annually and reach $220.21 billion by the end of 2022 (Research and Markets).
Types of cloud security measures
Similar to securing a local IT system, cloud security can also be classified into three categories: cloud security, cloud application security, and cloud access security.
Cloud security is a broad term for protecting all the layers of a cloud system excluding the application. A key part of cloud security involves securing your databases by encrypting them.
{Penta Security’s D’Amo Cloud combines multiple encryption technologies to offer the optimal encryption framework for cloud databases.}
Cloud application security specifically protects the application layer of the system, protecting the web application from web attacks like DDoS, SQL injection, and cross-site scripting (XSS).
{Penta Security’s WAPPLES SA is a web application firewall designed for the cloud environment, effectively protecting cloud-based web applications. For those without the time and expertise to manage a web application firewall, Cloudbric is a SaaS security application itself that provides protection for cloud-based web applications.}
Lastly, cloud access security makes sure that only legitimate users are allowed to access the program. An authentication module determines who is allowed to access a program, while a cloud access security broker monitors all user activities.
{Penta Security’s ISign+ Cloud is a single sign-on authentication solution optimized for the cloud.}
What kind of cloud security solutions do I need?
IaaS, PaaS, and SaaS require different levels of security measures. As seen in figure 1, for IaaS and PaaS, the user is responsible for managing and securing their own database, instead of sharing a public database, which is why these are also called private clouds. Under such environments, it is often necessary for the user to adopt all three types of cloud security measures. In addition, in an IaaS environment, the user is also responsible for managing their own operating systems and patching them.
Under a SaaS environment, the cloud provider is responsible for securing all the layers of the cloud system. However, the provider does not take responsibility for data lost or stolen from the user’s end. Thus, it is important for the user to set robust passwords and keep their login credentials at a safe place.
Some vendors offer cloud security services along with their main service. Thus it is always important to take these into consideration when choosing a service, and find the appropriate security solutions for the services you choose.
On the one hand, the more responsibilities the vendor takes (i.e. SaaS), the safer it is – large cloud providers at Silicon Valley have some of the most robust security infrastructures in the world. On the other hand, these providers also receive more attention and face more threats. So there isn’t a definite answer as to which is the safer service. Nonetheless, SaaS applications are most likely not sufficient enough for most organizations, and that they can also be really costly. In reality, most organizations adopt a combination of IaaS, PaaS, and SaaS.
The bottom line is to choose the right cloud services for your business needs, and to always find the appropriate balance of security measures to secure them. If you are unsure of what security solutions to apply, feel free to contact Penta Security for help. Click here to contact us.
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Web Application Firewall for Cloud: WAPPLES SA
Database Encryption: D’Amo
Authentication: ISign+
Smart Car Security: AutoCrypt
