Top 7 Most Common Types of Cyberattacks on Web Applications
Cyberattacks on web applications are increasingly common. As more and more governments and businesses move their services online, web applications become an easy target for cybercriminals. Web attacks are one of the biggest threats to corporate security and data security. They can lead to a wide range of devastating consequences from service disruptions and shutdowns to information theft and data manipulation.
Ever been overwhelmed by all those complicated cybersecurity terms shown on the news, and head to Wikipedia only to get more confused? Here we are explaining in the simplest way some of the most common cyberattacks aimed at web applications.
What is a web application?
A web application is an application program that is installed on a remote server and delivered through the internet, with the website being the user interface. Think about email, social media, and e-commerce sites – you are basically using these applications on the web without having the need to install it locally on your computer.
Simply put, if your interaction with a website involves the request for data, it is likely a web application. For example, most web forms are web applications; when you enter your information in a login form and click the “login” button, you are sending a request to the server to extract your data and reflect them on the user interface.
7 common types of web attacks
SQL injection attack
An SQL injection attack is when attackers inject malicious SQL scripts1 into a web application to gain access to the database stored in the server. A common way for hackers to do that is by injecting hidden SQL queries2 in web forms (e.g. login form). Usually, when a user inputs their information in the form and hits the “login” button, an SQL query would be sent to the database to request that user’s information. However, when hackers inject a malicious SQL query, they could request all kinds of data from the database. By then, the hacker would be able to easily view, change, or delete data and potentially paralyze the entire system from functioning. Since most web applications have databases stored in their servers, these applications become attractive targets for SQL injection, leading to breaches of sensitive information.
1 An SQL script contains a set of SQL commands saved as a single file.
2 An SQL query is a request for data or information from a database.
Cross site scripting (XSS) attack
A cross site scripting attack occurs when a website has a vulnerability that allows the injection of scripts. Attackers exploit such vulnerabilities and inject malicious JavaScripts into the website’s database. When a user later requests these data, the user’s web browser would execute the malicious JavaScript. This would allow the attacker to steal the browser’s cookies for session hijacking1. Hackers can then use the session information to exploit additional vulnerabilities, possibly gain network information and control the user’s computer. This is especially critical for the corporate environment as one XSS attack could compromise the whole network.
1 Every time a user logs into an account of a website, the browser records it as a session and stores it as cookies. Session hijacking is when an attacker steals the browser’s cookies and tricks the browser into believing it is the same session as the original one, allowing the attacker to gain full access to the user’s account.
Denial-of-service (DoS)/ distributed-denial-of-service (DDoS) attack
A denial-of-service attack is when an attacker sends an enormous amount of traffic to a website in an attempt to overwhelm the hosting server to disrupt and even paralyze service. What’s more, for websites renting cloud servers with volume-based costing, they could be charged with an astronomical cost by the service provider. A distributed-denial-of-service is the same concept, except that this time, the hacker gains illegal control over a number of computers to launch the attack on a larger scale.
Different from other cyberattacks, hackers do not receive any direct benefit from DDoS attacks. Such attacks are commonly used by state-sponsored hackers whose goal is to disrupt service of foreign governments and organizations. For example, events like the Olympics are common targets. According to a Cisco report, the 2016 Rio Olympics websites suffered from 223 large scale DDoS attacks. Japan is also getting ready for the 2020 Tokyo Olympics by setting up a cybersecurity council (GovInsider).
OS command injection attack
An OS command injection is when attackers input operating system (OS) commands into the server that is running the web application. It differs from an SQL injection because it enters from the server-side instead of the application-side. However, the consequences are very similar to an SQL injection attack, where attackers can take full control of the application. Attackers can command the application to display sensitive information, as well as modifying and deleting data. The application can also be utilized to compromise other parts of the corporate network, leading to further attacks within the organization.
LDAP injection attack
Lightweight Directory Access Protocol (LDAP) is a software protocol mostly used for corporate intranets. It enables anyone on the network to find resources from its directory, such as other individuals, devices, files, as well as usernames and passwords as part of a single sign-on (SSO) system. An LDAP injection attack is when a vulnerability allows attackers to send queries without proper validation. Attackers could then alter the queries to gain access to critical resources, leading to devastating consequences.
Brute force attack
A brute force attack, sometimes called a password attack, is one of the simplest forms of web attacks. The hacker simply tries different combinations of usernames and passwords repeatedly until it logs into the user’s account. Take a standard eight-digit password, for example, 52 letters (uppercase and lowercase) and 10 digits provide 62 total possible characters, making a total of 628 = 2.1834011×1014 possible combinations. Of course, it would take years for a single computer to try all the combinations. But when hackers gain control of multiple computers or develop a powerful software-based computing engine, things can become very easy.
Zero-day attack
A zero-day attack exploits publicized (or sometimes known through other means) software flaws before they are patched with software updates. Wondering how it got its name? Well, if the day of the software update is seen as “day one”, then an attack that comes before the update is said to occur on “day zero”, making it a zero-day attack. Since these attacks target flaws that do not yet have a fix, they can be difficult to deal with in the short run. Think of it as a new virus without any vaccine or treatment.
Many zero-day attacks target Microsoft Windows right after a software update is released, leaving those who do not update immediately wide open to the attacks. The next time you get notified of a software update, think twice before you click that “postpone” button!
How to prevent a web attack?
There are just too many types of web attacks for an organization’s IT management to handle one by one. This is why a complete solution that protects web applications from all types of attacks is necessary. A web application firewall (WAF) blocks all kinds of abnormal traffic from entering the web server.
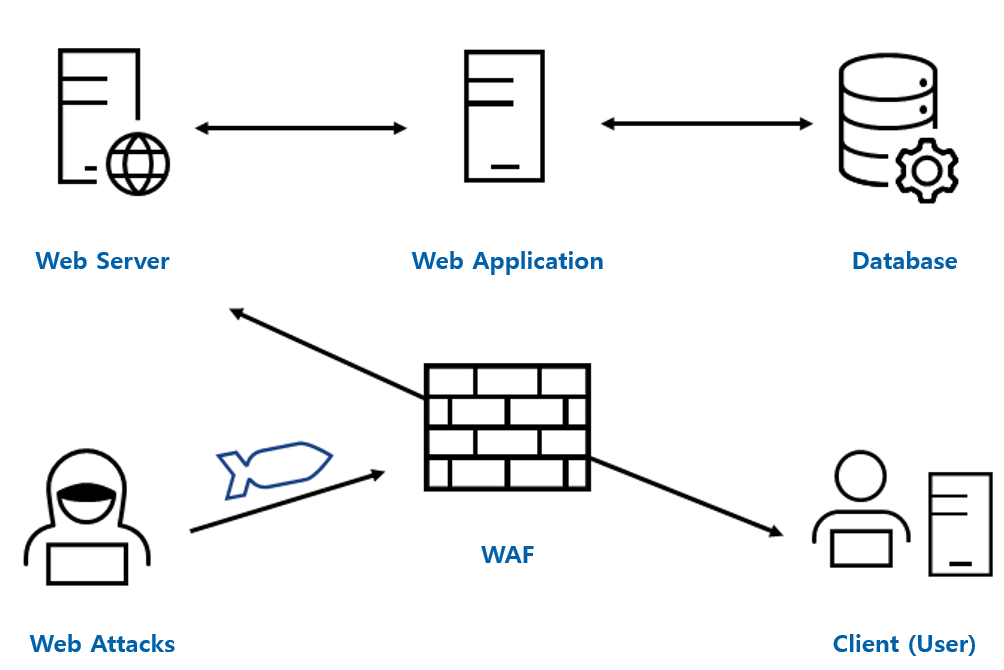
You may want to ask, how does a WAF identify all kinds of web attacks? You are right, many of the WAFs out there, especially the ones using older technologies, require the IT management to manually update its signature lists, and only block those attacks recorded on its list. These WAFs can be inefficient and get easily outdated.
Penta Security’s WAPPLES uses machine learning technology to automatically update the signature lists. Even when a hacker changes their attack pattern, artificial intelligence would still be able to identify these new attacks correctly. WAPPLES’ twin brother WAPPLES SA is optimized for those using cloud-based web servers. Having been in the market for 15 years, and as the market share leader in Asia Pacific, WAPPLES is one of the most reliable choices for WAFs.
Click here to learn more about WAPPLES.
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Web Application Firewall for Cloud: WAPPLES SA
Database Encryption: D’Amo
Authentication: ISign+
Smart Car Security: AutoCrypt
