March 2022, Issue II 1. Samsung suffers massive leak of source code by LAPSU$ […]
Read moreCurrently browsing: Blog
[Security Weekly] NVIDIA Credentials and Proprietary Information Stolen by LAPSU$ Hacker Group
March 2022, Issue I 1. NVIDIA credentials and proprietary information stolen by LAPSU$ hacker […]
Read moreTypes of Open-Source Databases and Security in Them
The term open-source software refers to software users can modify and leverage thanks to its […]
Read moreWhat Is Cryptojacking and How to Protect Your Enterprise and Devices
Cryptojacking: The Silent Intruder Cryptojacking, as the name suggests, is when criminals gain unauthorized access […]
Read more[Security Weekly] Airport Services Giant Swissport Struck by AlphV/BlackCat Ransomware
February 2022, Issue II 1. Airport services giant Swissport struck by AlphV/BlackCat ransomware Zurich-based […]
Read more[Security Weekly] Cyberattack at Red Cross Compromises Personal Record of 515,000 Vulnerable People
February 2022, Issue I 1. Cyberattack at Red Cross compromises personal record of 515,000 […]
Read moreHow to Prepare for the Rise of Ransom DDoS Attacks
Increasingly Powerful DDoS Attacks Distributed denial-of-service (DDoS) has long been a popular cyberattack method used […]
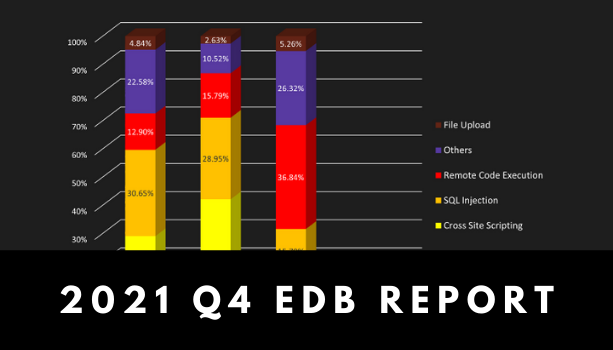
Read moreInfographic: Web Vulnerabilities in Q4 2021
We saw a downward trend in the overall number of web vulnerabilities during the last […]
Read moreTop 3 Ways to Protect Big Data from Security Threats
As it becomes more crucial for companies to adopt advanced technologies to thrive in this […]
Read more[Security Weekly] Ukrainian Government Suffers Massive Website Defacement Attack
January 2022, Issue II 1. Ukrainian government agencies suffer massive website defacement attack Over […]
Read more